
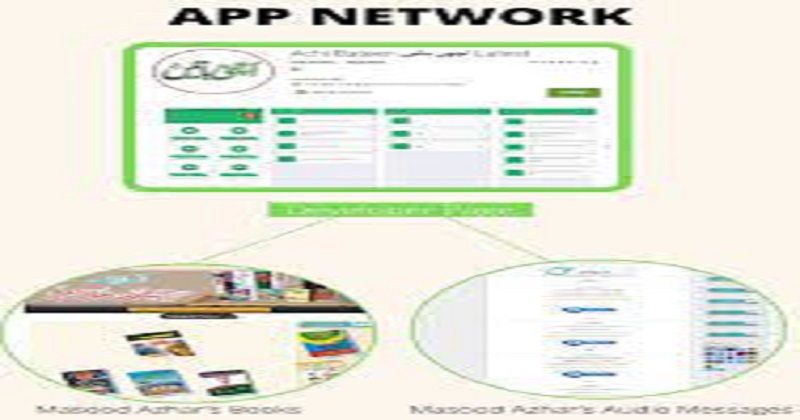
Android users around the world can download a mobile application associated with the Pakistan-based terrorist group Jaish-e-Mohammed (JeM) from the Google Play Store. The application ‘Achi Bateen’ offers Islamic teachings via a mobile application called a digital platform. However, it does not openly affiliate itself with the organization. A developer page, however, shows content linked to JeM chief Maulana Masood Azhar.
This site also provides links to external websites that feature books, literature, and audio messages from Masood Azhar and his associates. The United Nations Security Council (UNSC) has sanctioned JeM since 2001. The United States Department of State has also identified the group as a Foreign Terrorist Organization (FTO).

JeM-linked is live on Google Play
The Android application was initially released on December 4, 2020 at the Play Store. Since its release, it has received more than 5,000 downloads. A free app offering quotes, messages, and links to the books of several Islamic preachers from Pakistan is available for download. From mainstream names such as Ash Maulana Tariq Jamil to the teachings of late hardliner Rashid Ahmed, the content varies greatly.
The app’s developer has created a blog page that is hyperlinked to the app’s description page. A web page on the site contains old blog posts by Masood Azhar, under a pen name known as ‘Saadi’, a pseudonym well associated with the JeM leader. There are Links to two external websites on the app. Audio messages by Masood Azhar spanning the years 2001 to 2019 can be heard on one of them. The recordings also feature Abdul Rauf Asghar, Masood Azhar’s younger brother and head of JeM operations, and Talha Saif, his close associate. Several related books allegedly written by Masood Azhar are linked from another page hosted by the developer’s blog.
Innefu Labs, an information security firm, has handled an analysis of the application for India Today and has discovered it is communicating with a server in Germany. According to Tarun Wig, co-founder of Innefu Lab, the application is connected to servers in Contabo’s data centre in Germany, a company that has been in the news for ignoring copyright claims made by different individuals. The app, according to Wig, asks for multiple permissions that are different from application functionality. The reason for doing this is that you want to add additional functionality without asking for permission. It is similar to what is happening when the Chinese UC browser application is installed for the first time. Once the application is installed for the first time, the application container is able to run different classes in the application.
Read more: ‘Lost at sea’: Men survived for 29 days on oranges, coconuts, and rain water
Once installed, the app accesses both network and GPS (Global Positioning System) location — when GPS is active — of the mobile device. The app can start automatically once the user starts his device, and it continues to run in the background as well. It has access to the phone’s approximate and precise location, network, storage, media, and other files. “An app of this sort if identified should be immediately reported to Google that will remove the application from Play Store and also inform users for the same,” added Wig.

Post Your Comments